 DDoS Protection
DDoS Protection
Stop people from stopping you
Unmetered, highly available DDoS mitigation.
Routing is not mitigating
Providers that don't have enough capacity will often change routes when you're suffering an attack. Instead of routing, Latitude.sh will mitigate, meaning no increase in latency for you.
No attack is too big
With 7 Tbps of capacity, Latitude.sh's scrubbing centers are equipped to handle any distributed attack, no matter its shape or form.
Included and extensible
All Latitude.sh servers offer mitigation of DDoS attacks at no extra cost, so you'll always be protected.

No matter the attack, we can handle it.
Network level
- TCP Flood
- UDP Flood
- ICMP Flood
Reflective/Amplified
- DNS Flood
- NTP Flood
- SNMP Flood
- SSDP Flood
Fragmented Packet
- Overlapping
- Missing
- Too Many
Application Layer
- Repetitive GET
- Slowloris
- SlowRead
Specially Crafted Packet
- Stack
- Protocol
- Buffer
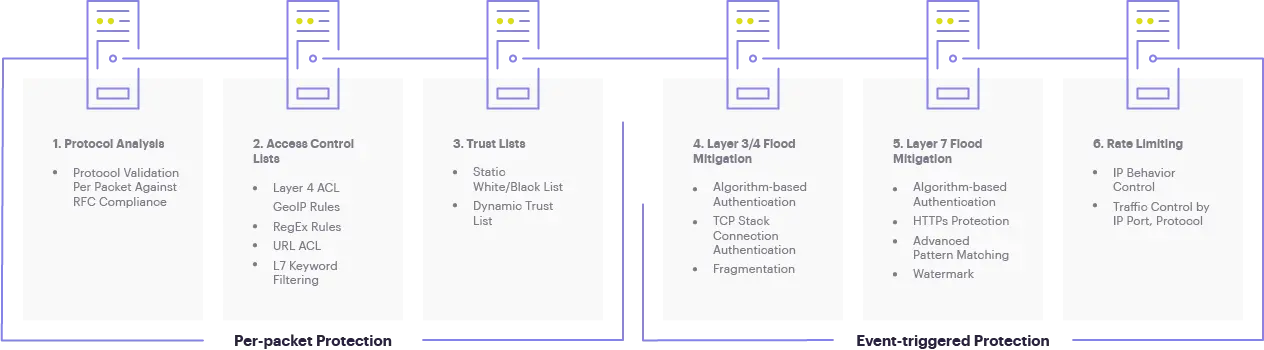
Managed Defense Mechanisms
Latitude.sh DDoS Protection service is fully managed. On top of traditional management features such as IP blocking, ACLs, null routes, blackholes, and unused ports disabling, it goes further with complete protection of layers 3, 4, and 7.
Ready to get started?
Create an account and start deploying bare metal servers globally.Or, contact us to design a custom solution for your business.