Blog/
Introducing Remote Access, the safest way to access your servers remotely
September 23, 2019
Prior to today, when you needed to access your server remotely through IPMI, you had to contact our team, who would then create a VPN session and share temporary IPMI credentials that you could use. Since that is not ideal when you need to change things quickly on your infrastructure, we have been working hard to increase the speed and safety of all of these processes.
Today, we are proud to announce the next step in enhancing the management of your servers from the dashboard and API: Latitude.sh Remote Access.
When you go to the dashboard and select a server, you will now find the Remote Access option.
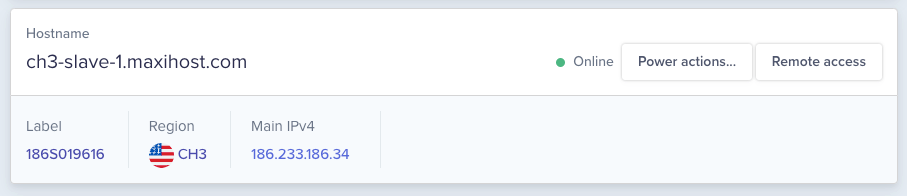
Clicking on it will take you to a page where you will set up a VPN session and obtain the credentials to gain access to the IPMI instantly.
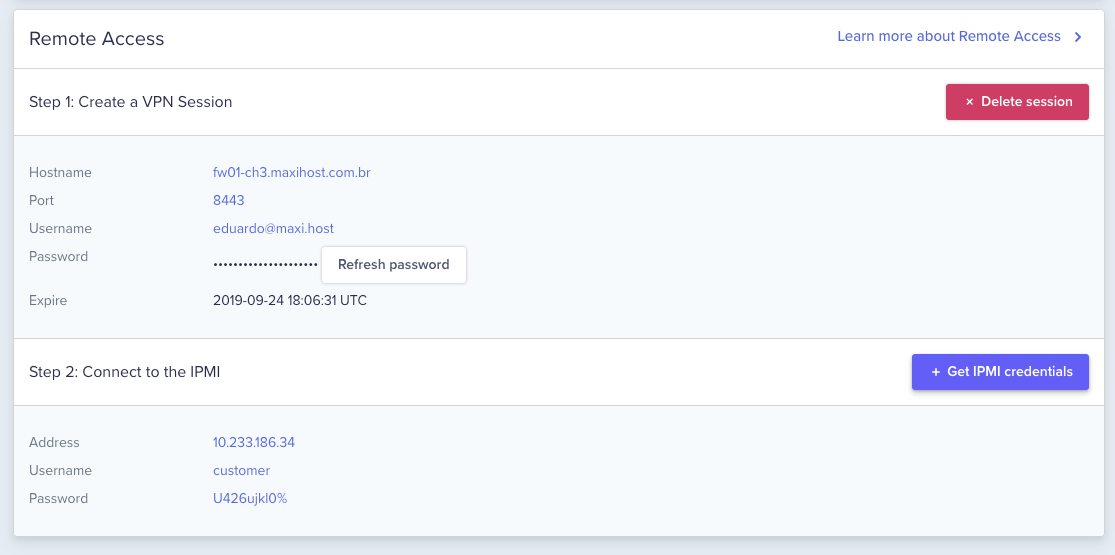
How we're making the process safer
IPMI is notoriously insecure, but it is still the best way to manage a server when you lose SSH access or need to make changes to server operation.
In order to protect you and your servers, we have built an incredibly safe way to access your servers remotely. Here are some of the measures we took to protect you:
IPMI IP addresses are always private. We require that you create a VPN session before getting the IPMI credentials.
When you create a VPN session, we make sure that session only has access to the IPs that exist in your account, meaning you cannot access anything from a private network that is not assigned to you.
VPN sessions and passwords expire after 24 hours. We do not store passwords anywhere.
Every time you request your IPMI credentials, we change the IPMI password. Again, we do not store IPMI passwords anywhere.
When providing remote access for Bare Metal, providers usually have to compromise on something, either removing IPMI access and only providing a console, or simply disabling everything. We are glad we have found a solution that keeps your servers safe while giving you full control of the underlying infrastructure.
If you are interested in learning more, see the documentation. You will find more information about how to use Remote Access.
Also, don't hesitate to share your feedback with the team who built this. Send an email to the Engineering team.